


Recently, Israel was shaken to the core from a heinous gang rape of a sixteen year old girl. As the investigation unfolds, reports of images and videos of the crime surface. Sadly, this type of crime and the documentation of it, occurs in every country. Survivors of sexual violence face even more emotional damage due to the existence of digital imagery of the crime that took place. Videos and photos are forwarded and posted on instant messaging and social media, and often cloud platforms are helpless (or choose not) to do anything to stop this.
Until now.
I will preempt by saying that there will always be bad people in the world who will find a way of doing bad things, and posting illegal and illicit images of children on the darknet. I am aware that at the moment at least, nothing can be done to stop them, technologically. I do know however that the technology exists to assist popular cloud storage platforms in removing ALL of those illegal images from their databases, and that - morally - it should be our mission to help them do so.
The technology is called blockchain. A decentralized and encrypted database created by multiple law enforcement agencies by each sharing their proprietary databases, can allow cloud platforms to scan and tag their images while being uploaded, in order to locate and delete child pornography that has been confirmed as illegal. In addition, it would allow them to scan and tag this type of content that is already stored and distributed across their platforms.
There are few ‘no brainer’ cases for blockchain. In fact many use cases would be better served using a centralized as opposed to a decentralized solution. However, when multiple parties who have a trust issue need to work together and want visibility on their work - blockchain is the obvious answer. I believe that we have the perfect use case here.
Multiple law enforcement agencies from around the world each have databases of illegal child sexual imagery. However, cloud platforms are not too keen to have law enforcement or government interfere with their client’s private caches, nor do enforcement agencies have a global reach. Distributing or viewing this imagery is illegal - to the point that even if a victim's family scans the internet to see if images still exist, they can be charged with illegal conduct for doing so. So how do we create a situation where multiple law enforcement agencies, locally or globally, can collaborate on a database of illegal images for cloud platforms to easily and efficiently access and remove all traces of child sexual exploitation material - but without actually having access to the material itself? The answer is with the combination of PhotoDNA and blockchain.
PhotoDNA is a technology developed by Microsoft and Dartmouth College to create a unique digital fingerprint of a digital image (or a video for that matter). Thus, any set of images may be analyzed and compared in order to determine their similarity. This means that even if an image was manipulated (e.g., cropped, resized, filters applied, etc.) it can still be automatically identified as a variation of another image that looks different, but has the identical (or similar enough) digital fingerprint.
As impressive as this may be, it is blockchain that takes this solution to the next level, as it allows law enforcement agencies from around the world to easily and efficiently collaborate. While some of them have databases of illegal imagery, it seems that they don’t share them with each other, at least not as often as one would expect them to. This is exactly where blockchain shines by providing the platform for building a distributed shared database that everyone equally owns. Put differently, it would be a joint global effort in which each law enforcement agency shares the fingerprints it has collected and in return, gets full access to all the other fingerprints that other agencies have. However, no single agency is “in charge” or “owns” this database. They all equally do. Once it is up, they can easily upload new digital fingerprints, and of course benefit from the ones that other agencies have.
Once the database is up and running, cloud storage platforms will get read-only access to it and could immediately start scanning and tagging illegal imagery, based on this globally confirmed set of digital fingerprints. Moreover, they would be expected to do so for each file that is uploaded from now on. Furthermore, each enforcement agency could determine the set of rules that cloud storage platforms would be required to adhere to in their jurisdiction, making the platforms’ lives easier in that aspect.
It is worthwhile emphasizing that it is not a database of images but of digital fingerprints. Without getting into technical details, the connection is unidirectional, i.e. it is easy to generate a fingerprint from an image, but impossible to reverse-engineer the image from a fingerprint. Therefore, a fingerprint by itself is meaningless and cannot be traced back to an image. This results in a database that aside from being highly secured by nature, being blockchain-based, provides no incentives to be hacked by someone who’s looking to own or distribute illegal content, and also removes the concern of sharing the actual material which is illicit or illegal in nature.
The chart below shows the process in the eyes of a user who’s trying to upload an image to his cloud storage drive.
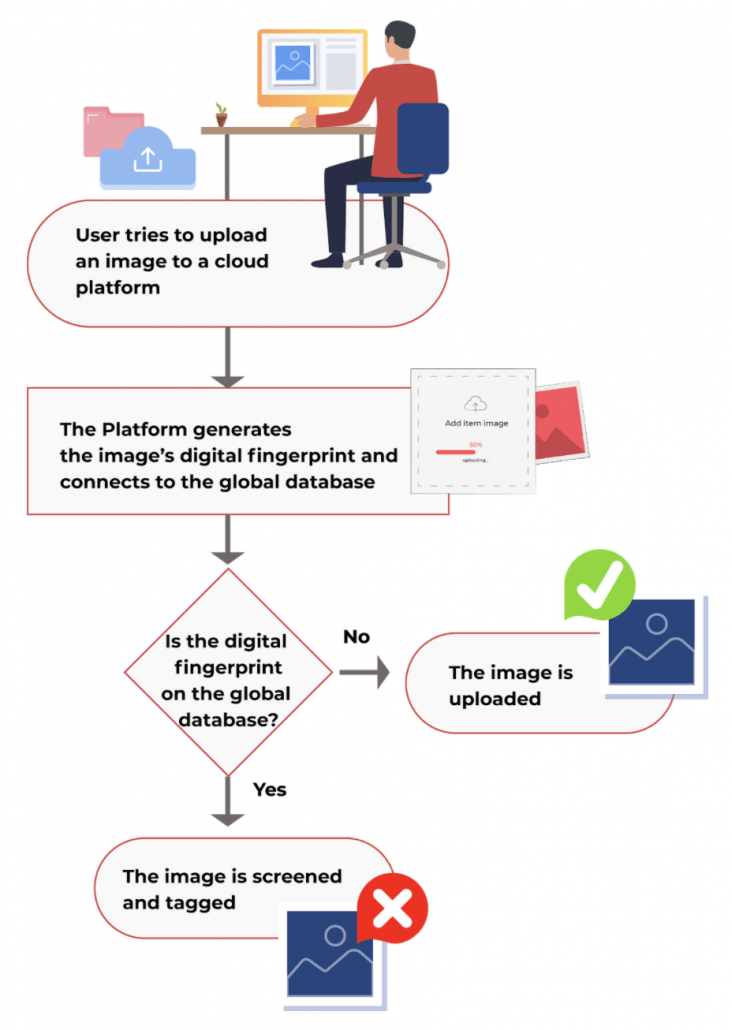
Finally, to top it all, the entire process will be completely transparent. Meaning that enforcement agencies can see which fingerprints were added by who, cloud platforms will know exactly which fingerprints they need to screen in which jurisdictions and enforcement agencies could easily check whether their restrictions are properly enforced by cloud platforms. Perhaps, that should be the main catalyst for using blockchain for this use case.
Sadly, as of now there is no perfect solution that will eliminate the problem of child sexual imagery from the internet. Evil people always find a way of doing evil things, and they will go to dark places of the internet to do so. But we can - easily - remove these images for the majority of users who do not have the technological expertise to access the darknet. The Hexa Foundation is in talks with both government and enforcement agencies exploring the opportunity of using the Orbs blockchain as a solution that will help cloud platforms remove these images from the view of the everyday internet user. As the saying goes, the enemy of the good is the perfect. We can not take away the crime, but we can help remove hurtful and haunting documentation of it from surfacing. We actually can, today, make a dent in this horror, and so we should rally behind our law enforcement and our social media service providers - and help them do so.
···

Hexa Foundation is a not-for-profit organization focused on using blockchain to create social impact. The organization was co-founded by Netta Korin, who comes to the Foundation following years of experience in business, government and non-profit industries. Most recently, Netta worked as a Senior Advisor in the Israeli Ministry of Defense to General Yoav (Poly) Mordechai, Head of CoGAT, and has an in-depth knowledge of the socioeconomic problems in the Gaza Strip.
Prior to that position, Netta worked as a Senior Advisor to Deputy Minister Dr. Michael Oren in the Prime Minister’s Office in Israel, focusing on Palestinian issues. Netta has held board positions in several non profit foundations in both Israel and the United States. The Hexa Foundation is part of the Orbs Group. Both were created by the founders of Orbs, a blockchain platform for consumer applications. Orbs Group is the largest group dealing in blockchain solutions in Israel. The Hexa Foundation aims to use blockchain for social impact and harness the mind power of our ecosystem and network to help solve the region’s and the world’s most pressing humanitarian problems.
For more information please contact Netta Korin (netta@hexa.org)
···
© All Rights Reserved to Hexa Foundation Ltd. (CC)
The Hexa Foundation Ltd. (CC) permits the free use of this document, subject to the conditions set forth below.
The use of this document is permitted for private and personal use only. It is prohibited to copy and to use, or allow others to use, this document for any purpose, whether commercial or non-commercial, other than private and personal use.
The contents of this document are permitted for use on an as-is basis. The reader or any third party shall not have any claim or demand against Hexa Foundation Ltd. (CC) with respect to any of the contents of this document. Hexa Foundation Ltd. (CC), including its employees and representatives, shall not have any liability for any damage to the reader or any third party that occurs, directly or indirectly, as a result from the use of this document or the information contained therein.
We use cookies to ensure that we give you the best experience on our website. By continuing to use our site, you accept our cookie policy.